Many organizations leverage the business intelligence tool Microsoft Power BI to extract valuable data insights. But the more the data becomes accessible, the more is the risk of critical business information being misused or overshared by accident. Microsoft protects its clients from multiple threats using world-class security capabilities. They have employed over 3500 security researchers to implement sophisticated artificial intelligence models every day with approximately 6.5 trillion signals around the world to protect their customers against threats.
If you have a question on what is Power BI? Then you must know that it is the strength of Microsoft in security. The data protection capabilities of Power BI allow their customers to secure their data regardless of the fact from where or how it is accessed. It also enables you to –
- Microsoft information protection sensitivity labels are used in every Microsoft Product like Office and more so that the confidential information can be classified and labeled as sensitive in the Power BI tool.
- To make sure that your sensitive data is protected even after it is exported from the Power BI to Powerpoint, Excel, PDF, and other formats by enforcing the government policies.
- You can monitor and protect all user activity on the data labeled as sensitive with risk remediation, real-time alerts, and session monitoring with the help of cloud app security.
- Microsoft Cloud app security is used by security administrators with security investigation capabilities and data protection reports. It empowers them to improve their organizational oversight.
In this blog, we will be covering the two main aspects of data protection in Power BI. they are:
- Cloud App Security.
- Microsoft Information Protection sensitivity labels
Overview of Cloud App Security
The cloud apps security for Microsoft is renamed to Microsoft Defender for Cloud Apps. and not only the name is changed many aspects of Microsoft Security Services have been updated along with it. Being a Cloud Access Security Broker, Microsoft Defender supports various modes of deployment that include reverse proxy, log collection, and API connectors. It offers control over data travel and high visibility. Its sophisticated analytics comes in handy while identifying and fighting all kinds of threats to Microsoft and other third-party cloud service providers.
Best Microsoft solutions are integrated with Microsoft Defender for Cloud Apps and are designed by developers by keeping the security professionals in mind. It offers centralized management, innovative automation, and simple deployment capabilities.
What is a CASB?
Moving to the cloud is not only flexible for the entire organization collectively but also flexible for every team and every employee individually. Still, it brings many complexities and challenges in the path of protecting the data of your organization. It is the responsibility of an IT team to find supporting access in the protection of sensitive data. Then only they will be able to get the benefits of cloud app services.
This demands the right balance that could be brought by a Cloud Access Security Broker. They enforce the security policies of your organization to add some safeguards to the cloud services. This job is more like a gatekeeper that brokers access to your sensitive enterprise data in real-time between the cloud resources and the users irrespective of their location and device.
CASBs accomplish all of this by discovering and rendering visibility to the app usage and Shadow IT, protection against malicious factors, controlling the access to the resources of your company, enabling you to classify sensitive information and prevent its leak, assessing the compliance of cloud services, and monitoring all the user activities for any odd behavior or anomaly.
The security gap in the cloud services of any enterprise is addressed by CASBs. They provide microscopic visibility and control over the sensitive organizational data and all user activities. The scope of CASB covers everything including PaaS, laaS, and SaaS. CASB leverages top CRM systems, Enterprise resource planning solutions, enterprise social networking sites, content collaboration platforms, services desks, HR systems, and office productivity suites to cover SaaS.
And in terms of PaaS and laaS coverage, the popular cloud services providers’ API-based usage is governed by CASBs. This extends the governance and visibility of apps running on clouds.
Why would you need a CASB?
Understanding the overall posture for cloud across SaaS apps is not easy, you would need the help of your CASB. And do not forget that the governance of your cloud apps and Shadow IT discovery are the critical use cases here.
The management and protection of a cloud platform including their computer resources, network resources, data, storage, VMs, IAM, and more come under the wing of the organization. If your organization is already using or is considering adding the cloud apps to your network services portfolio then you must find yourself a CASB that could address the challenges that come with securing and regulating the environment. A malicious actor can get into your enterprise network in many ways using cloud apps and can steal or leak your critical business information.
Malicious actors would employ many methods and ways to extract data. So, you need to be prepared to protect your data and the users from the schemes of these malicious actors. A CASB would help with it as they offer a wide range of capabilities to secure the environment across the following segments:
- Visibility: The third-party applications would be able to log in, will identify all the users, will assign every user a risk rank, and assess cloud services.
- Data security: Enable you to identify sensitive information so that you can control it. It responds to the data as per the classification labels assigned to them.
- Threat protection: mitigating risk and malware, adaptive access control, entity behavior analysis, and user behavior analysis.
- Compliance: Guides in verifying the data residency, fulfilling the requirements for regulatory compliance, sending reports and dashboards for cloud governance demonstration.
The Defender for Cloud Apps framework
- Discover and control Shadow IT usage: First of all, identify what kind of cloud apps, PaaS, and laaS services your organization is using. Then monitor the usage pattern, assess all the risks. Look for exactly how much SaaS apps are exposed to what level of risks. After that, you need to manage them all to maintain compliance and security.
- Protect your sensitive information anywhere in the cloud: You need to identify, understand, classify and then protect the critical business data that is exposed. You might have to go beyond the implementation of traditional policies. You can also use automated processes as it can imply control over all the cloud apps in real-time.
- Protect against cyber threats and anomalies: You also need to identify the ransomware in the cloud apps by detecting any unusual behavior. Such behavior could also lead to rogue apps and compromised users. You must analyze all high-risk usage and keep such settings so that it will automatically remediate the risk to your company.
- Assess the compliance of your cloud apps: Your cloud applications should meet all the compliance requirements related to industry standards as well as regulatory compliance. You can limit access to the regulated data and prevent any kind of information leak to the apps that are non-compliant.
Architecture
Integrate visibility with the cloud using Defender for Cloud Apps. you can accomplish it by:
- Map and identify what kind of environment and cloud apps your company is using with the help of Cloud Discovery.
- Sanction and un-sanction your cloud apps.
- To gain the governance for the app and visibility to the apps you wish to connect to, you could use the provider APIS that comes with the easy-to-deploy app connectors.
- Now, get control over access and real-time visibility by using Conditional Access App Control protection inside your cloud Apps.
- You can have constant control if you set and fine-tune the policies.
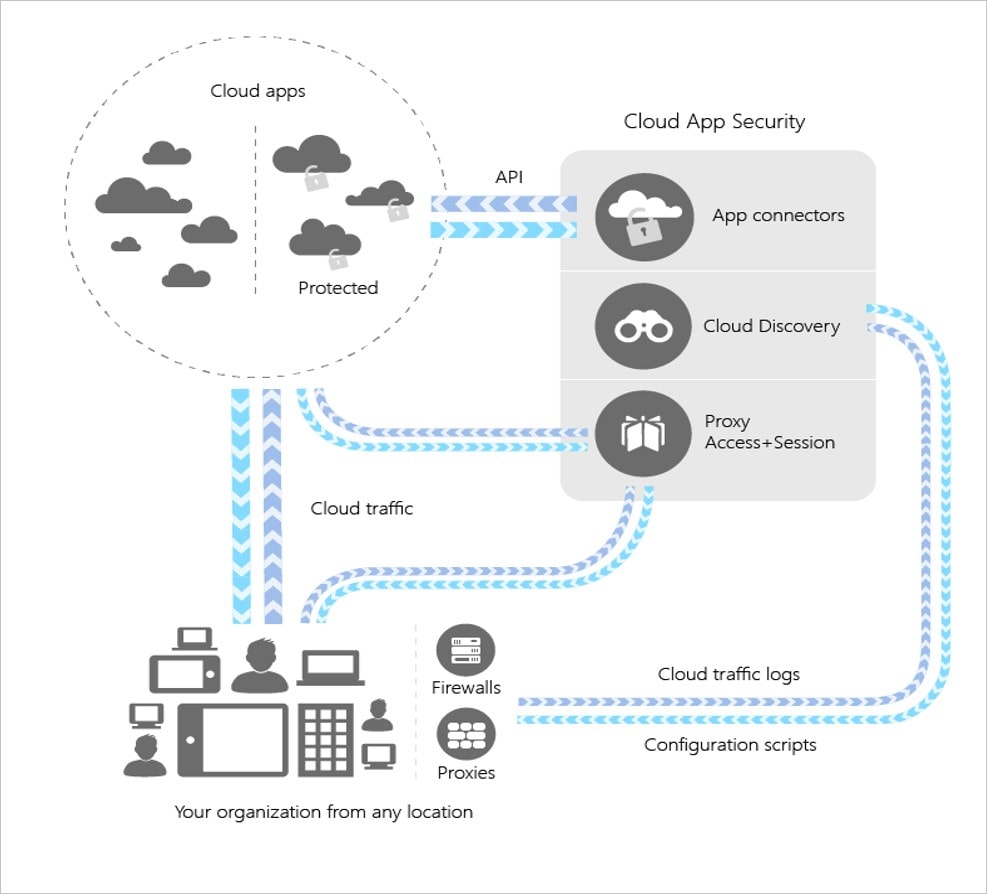
Cloud Discovery
Cloud Discovery is used to discover and analyze what kind of cloud apps your company uses and for that, they use your traffic logs. If you are mutually uploading the log files for analysis from your firewall or proxies then you will be able to create a snapshot report consisting of the cloud usage information of your company. If you want to set up continuous reports then you have to use Defender for Cloud Apps log collector that will regularly upload your traffic logs for analysis.
Sanctioning and un-sanctioning of an app
Defender for Cloud Apps would allow you to use a cloud app catalog where you can easily sanction and un-sanction all the cloud apps. The team of analysts at Microsoft has a very extensive and continuously growing Cloud app catalog with more than 25000 applications which are ranked and scored based on their industry standards.
You can analyze and rate the risk on your cloud apps on the basis of industry standards, regulatory certifications, and other best practices in your cloud app catalog. You can also customize the score and weigh all the parameters against your business requirements. Once you score your app, the Defender for Cloud Apps will inform you about the level of risk your app is at. There are more than 80 risk factors that affect your environment and your scoring is based on just them.
App connectors
The Defender for Cloud Apps is integrated with other apps using the APIs of app connectors from the cloud app providers. They are used to extend the control and protection over data. App connectors also allow you to access the data for cloud app analysis directly from the cloud applications. The Defender for Cloud Apps is authorized by the app administrator to access the cloud apps to connect and extend the protection capabilities. After connecting, the Defender for Cloud Apps will query the app to scan the entire data and account, cloud content, and activity logs. It could also offer some governance actions to solve issues, detect threats, and enforce policies.
Cloud providers give App connectors to Defender for Cloud Apps to use their APIs. Every cloud application has its framework and API limitations. To make sure that the apps perform at their best, the app providers work with Defender for Cloud Apps to optimize the APIs.
The Defender for Cloud Apps engines only uses the allowed capacity. Because it considers the limitations like dynamic time-shifting API windows, API limits, throttling, and more which are imposed on APIs by cloud apps. Certain tasks including the scanning of each file in the tenant need a large number of APIs that are spread over a long period. This will enable some policies to run for many hours or even days.
Conditional Access App Control protection
To have control over access and the activities performed in your cloud environment with real-time visibility, the Microsoft Defender for Cloud Apps uses reverse proxy architecture. This would provide you with the tools that will help you achieve the above-mentioned goals with Conditional Access App Control. It would secure your organizational data and protect your company:
- Block all the downloads beforehand to avoid any kind of data leak.
- Set the rules that would protect the data stored in and downloaded from the cloud with encryption.
- Obtain visibility to the unsecured endpoints. This will help you monitor the activities on unmanaged devices.
- Control access from non-corporate networks or risky IP addresses
Policy control
You can define cloud user behavior with the help of policies. They are designed to detect all suspicious points of data and activities, any kind of violations, and risky behaviors in the cloud environment. You can also accomplish total risk mitigation if you want by integrating remediation processes using the policies. The correlation between the information in the cloud environment, your remediation actions, and the policies are different based on their particular type.
Here, we conclude our section on the Microsoft Cloud App Security and now, let us move on to discuss another aspect of Data Protection in Power BI in this blog.
How sensitivity labels work in Power BI
Applying a sensitivity label on your Power BI content and files is similar to applying a tag on the resources with the advantages mentioned below:
- Customizable – Allow you to create various categories for multiple levels of sensitive data of the organization like general, public, private, confidential, and highly confidential.
- Clear text – The labels are in clear text which makes it easy for the users to understand how content would be treated under the sensitivity label guidelines.
- Persistent – Once you apply a sensitivity label on any type of content. It’s there to stay even if you export it to other formats like PDF, Excel, or PowerPoint files, or save it on desktop or download it to .pbix. It is the base of the implementation and enforcement of the policies.
Sensitivity labels in Power BI Desktop
You can also apply the sensitivity labels in the Power BI Desktop. Doing so will allow you to protect your data or content right from the moment you first start developing it. When you save any kind of work on the desktop with a sensitivity label and other associated encryption settings, the results are also applied to the .pbix file. If you secure your file with the encryption settings of the sensitivity label then no matter where your files roam or in what way it gets transmitted, the file will remain highly protected. Only those users will be able to open these files who have the essential RMS permissions. Although there are some considerations and limitations to it too.
It is recommended that you apply the relevant sensitivity label on the content on your Desktop before publishing it to any service or uploading its .pbix file anywhere. Because once you have applied a sensitivity label to your work, it goes where your data goes. And it will not only apply to the set of data but also to any specific report you have with your file. If your file or report already has any sensitivity label on it, it is your choice whether you want to keep them or overwrite it with another label from the Power BI Desktop.
If your .pbix file is never published on any service before but has the same name as any dataset or a report already existing on the services where you wish to upload your file, you wouldn’t be able to upload successfully. The only way you can upload your file is if you have the necessary RMS permissions to change the sensitivity label of the file.
The same can be said true in the opposite case. If you wish to download a .pbix file in service and load it onto your desktop, the label applied to that file in the service will also be applied to the downloaded file. Hence it will also be loaded with the file on your desktop. In any case, if the report and the dataset have different sensitivity labels in the service then the label with more restrictions will be applied to the downloaded .pbix file on your desktop. A label applied to the desktop is shown in the status bar.
Sensitivity label inheritance with the creation of a new content
If you have already applied a sensitivity label on any dataset or a report and then you create a new report or dashboard in the Power BI services then they will automatically inherit the labels from their parent datasets and reports. For example, if you have applied a Confidential sensitivity label on a dataset and now you create a new report on top of it then the report will automatically inherit the Confidential label from the parent dataset. The image below shows how the sensitivity label of a dataset is automatically applied to the newly created report.
Now if due to an error or other reason, the sensitivity label of the parent dataset or report is not applied on the newly created report and dashboards then also the Power BI can’t block the user from creating a new item in the service.
Inheritance from data sources
If the datasets in Power BI are connected to any sensitivity-labeled data from any source of supported data, then those datasets will directly inherit those labels. This means the data will remain secure and classified when it is brought to the Power BI. Azure Synapse Analytics, which was formerly known as SQL Data Warehouse and the AZure SQL database are supported here. The data in the services can directly inherit the labels of the data in these sources if they are connected.
Downstream inheritance of labels
Suppose you are creating any content from the dataset or a report in the Power BI services that already have a sensitivity label on it. In such cases, that label will be automatically passed down to the content built from it. This inheritance capability is called downstream inheritance.
This is one of the most crucial links in the end-to-end protection capabilities of Power BI. Downstream inheritance capabilities include inheritance upon exporting to various formats of the file, inheritance in building new content, inheritance from the source of data, and more for the application of sensitivity labels. This is to make sure that the sensitive organizational data is well protected throughout its journey from the data source to its consumption via Power BI.
Default label policy
Make sure that your sensitive organizational data is protected and governed comprehensively. Power BI also allows the companies to create default label policies that would apply a default sensitivity label on unlabeled content automatically. Currently, only Power BI Desktop supports the default label policies.
Mandatory label policy
The mandatory label policy states that labeling content in the Power BI is compulsory. When an organization labels the Power BI content, it enables them to protect and govern their crucial data effectively.
Programmatically setting and removing Admin APIs
An organization needs to classify every content in the Power BI and apply sensitivity labels on them to meet the compliance requirements. Fulfilling this can be very challenging for the tenants with huge chunks of datasets in Power BI. Admins use the admin REST APIs from Power BI to programmatically set or remove the sensitivity labels on various artifacts in Power BI.
Activity Audit
Every activity on the sensitivity label of a dataset, dashboard, dataflow, or report is being recorded in the Power BI’s audit log including its application, removal, or any other changes. The unified audit log or the activity log of Power BI is used to track all these activities.
Sensitivity labels and associated protection capabilities on exported data
According to the encryption settings to the label files, whenever you export the data from Power BI to PDF, PowerPoint, or Excel files, the sensitivity label on the Power BI data is automatically applied to the exported file too. Hence your exported sensitive data remains secure no matter wherever or whenever it is shared.
Only the owner of the file gets the permission to change the sensitivity label settings, if the user who exported the file is different then the Power BI would only allow them to access and edit the file.
If you have downloaded the .pbix file in the service and the sensitivity label of the downloaded report and its dataset is different then the label with more restrictions will be automatically applied on the .pbix file. But the sensitivity labels and the protection capabilities will not be applied if you export the data from the Power BI to any unsupported path like exporting the data to .csv files.
The content marking won’t be added to the exported file when a sensitivity label is applied to it. But if you configure the label to apply content markings then the Azure Information Protection unified labeling client will automatically apply those markings whenever the file will be opened in the Office desktop applications. Even if you are using built-in labeling for web apps, mobile and desktop, the content markings will not be applied automatically.
If a label is not applied to the data then its export to a file will fail. You can click on the dashboard or report option in the middle of the title bar to check whether or not the export has failed because the label wasn’t applied. If you see a dropdown opening containing the information – “Sensitivity label can’t be loaded” if the label wasn’t applied on the data. The reason why the application of the label failed can be that the applied label can be an unpublished one or it might have been deleted by the security admin or it might just be a temporary system issue.
Inheritance in Analyze in Excel
You can create a PivotTable either directly from Excel or through Analyze in Excel from Power BI with a live connection to the dataset. The sensitivity applied on the Power BI dataset will be inherited by your Excel file with other associated protection capabilities. Later, if the sensitivity label on the Power BI dataset has been changed to a more restrictive one then the label on the Excel file that is linked to the dataset will automatically get updated once you refresh your data.
But if you have applied any sensitivity label on the Excel files manually then it won’t get updated automatically when the changes are made in the dataset to which it is linked. Only a banner will appear to notify you about the changes that have been made related to the sensitivity label on the linked dataset with a recommendation to do the same on your Excel file too.
And as we already discussed in this blog, in any case of inheritance the exported or linked file will inherit the more restrictive label only. If by any chance, the dataset has a lesser restrictive sensitivity label in comparison to the label applied on the Excel file then inheritance of the label or update would not take place. A file would never inherit the lesser restrictive sensitivity label than it already had beforehand.
Sensitivity label persistence in embedded reports and dashboards
The reports, dashboards, and other visuals from Power BI can be embedded easily to various business applications like Microsoft SharePoint, Teams, and even on your company website. Here too, the sensitivity label applied on the reports or dashboards will be seen in the embedded view. And its protection capabilities will persist even if the data will be exported to the Excel file. Various embedding scenarios supported here include:
- Your company’s content
- Business applications like MS Teams and SharePoint
- Data from Power BI services
Sensitivity labels in paginated reports and deployment pipelines
You can also apply sensitivity labels to the paginated reports which are hosted in the Power BI services. When you upload the paginated report to the Power BI services, you have to apply the sensitivity label just as you would to any regular report. Additionally, the deployment pipelines also support the sensitivity labels. Here too, you can manage the labels while deploying the data from one stage to another.
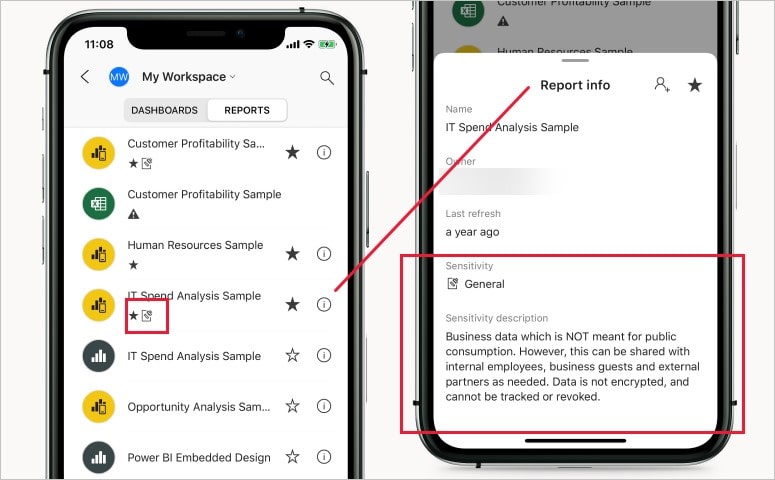
Sensitivity labels in the Power BI mobile apps
You can also view the sensitivity applied on the dashboards or reports in the Power BI mobile application. There will be an icon near the name of the report to indicate the sensitivity label. It would also show which type of sensitivity label is applied on the file and if you click on the info sign then you can find the relevant description about the data and its sensitivity label.
Label change enforcement
Only the authorized users have access or permission to change or remove the Microsoft Information Protection Sensitivity Labels in Power BI through file encryption settings.
Supported clouds
The residents of the global clouds or public clouds can use the sensitivity labels. Apart from that, the following nation clouds support such settings:
- US Government: GCC, GCC High, DoD
- China
No other nation’s clouds currently support the sensitivity labels.
Creation and management of Sensitivity Labels
Using Microsoft 365 compliance center, you can create and manage the sensitivity labels. You just have to navigate to the Classification option where you would find the sensitivity labels option to access the labels from any of these centers. All the Microsoft services like Office 365, Azure Information Protection, and Office apps use these sensitivity labels. If your company uses the Azure Information Protection Sensitivity Labels in Power BI then you have to relocate them to one of the previously listed services.
Custom help link
Sometimes it happens that your users might not understand the purpose of these labels and how they work. So to provide a better understanding to them, you can put a Learn More option with an URL at the bottom of the sensitivity label menu so that they can see why you have applied the label to the file or data.
Final Thoughts
There are many more aspects of data protection in Power BI but the two points we discussed in this blog, sensitivity labels, and cloud apps security pretty much cover most of it. If you wish to know more, you can visit the official website of the service provider. And in case you have any doubts or suggestions, share them with us in the comments section below.








