The most common root cause is poor file security or poor configuration selection in terms of the ways IIS should access the file content while investigating site infections or defacing on a Windows Servers. You can prevent this in an easiest way by simply starting a secure site.
To setup a website in IIS is very easy but several default settings aren’t best in terms of security or easy management.
Also, there are some practices that were considered essential or standard but now aren’t important or weren’t necessary at first too. Therefore, we recommend that you follow these steps for setting up a website for ensuring that it is correctly and securely set up. Though you might find some of these setting or permission change changeable, they work for systems that host multiple domains or multiple tenants as they avoid any cross-site file access.
Add the Site to IIS
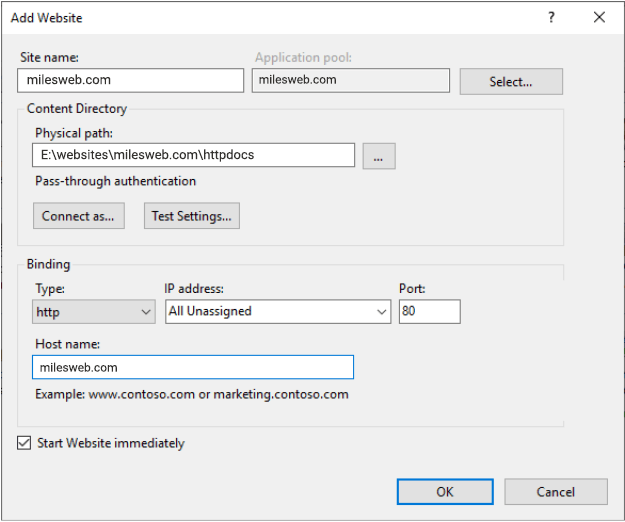
For adding a website in IIS (Internet Information Services), go to the IIS manager, right-click on Sites, and select Add Website.
While adding a site to IIS, it is recommended to use the domain name as the “Site name” to identify easily.
Under the “Physical path”, mention the path where your website content is located or use “…” to navigate and select the folder.
Note that you don’t need to modify configuration options under “Connect as…” and “Test Settings…”.
While configuring site bindings, it is recommended to select a specific IP from the “IP address” drop-down. But this is considered to be an outdated practice typically in terms of how SSLs used to require dedicated IPs. This isn’t necessary now and can actually lead to problems when getting into replication or highly available configuration.
Therefore, it is best to leave IP addresses set to All Unassigned and enter the domain name that you want to host in the “Host name” field.
Remember that you can enter only one value here. You can add additional host names after the site is created. For this, just right-click on the site and go to Bindings. Further, you can select “https” instead of “http” based on your needs.
Set the Anonymous User
In technical terms, this is all you need to do for setting up a site in IIS. But the site may or may not work and the security settings on the site are not best. The next step while securing your site is to configure the IIS user that will access your files. For this, it is important to change the associated Anonymous user and make a few security changes on the content folder of the website.
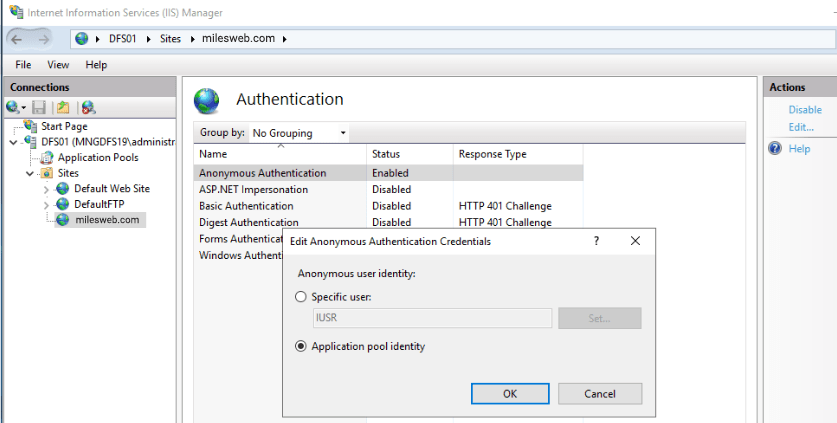
Select your new site on the left in the IIS. Then in the main window double click on Authentication, select Anonymous Authentication, and then click “Edit…” on the right action bar.
What is IUSR in IIS?
A new site in IIS utilizes the IUSR account by default for accessing files. This is a built-in shared account typically used by IIS for accessing the file content. This indicates that it will use the application pool’s identity (user) for accessing file content.
It doesn’t matter if you leave this configured in case you want to host just a single domain. But for hosting multiple domains, this isn’t secure as it would then be possible for any site that uses the same account to access files from another site. Therefore, as a standard practice it is recommended to switch away from using the IUSR account for sites, instead of selecting “Application pool identity” and clicking OK.
As an alternate option, you can manually create a user on the system for each site. But for an additional user- you need to manage the credentials, configure permissions for two users (the application pool user and the anonymous user) and possible complications with password difficulty and rotation needs that your server or organization may have.
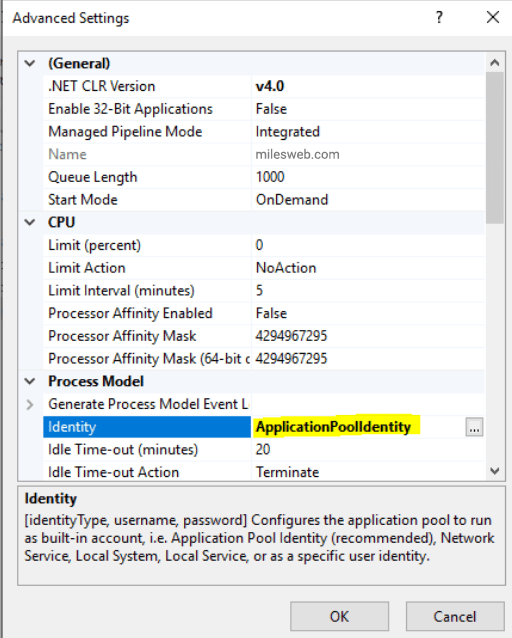
You don’t need to configure anything further in IIS in terms of security but still go through the application pool settings quickly. For checking the settings on the application pool, in IIS, go to the left menu and select Application Pools, select the application pool for the site you created (typically the same name as the name of the site) and on the right action bar, click on “Advanced Settings…”.
Here, the related setting is the identity and by default it is “ApplicationPoolIdentity”. It means to access the file content, IIS and the associated application pool will use a hidden and dynamic user based off the name of the application pool to access files. This user can only be used by IIS, has no associate password and only has the access to files that are specifically granted to it. Hence, it eliminated the requirement of managing system users and credentials.
Set Folder Permissions in IIS
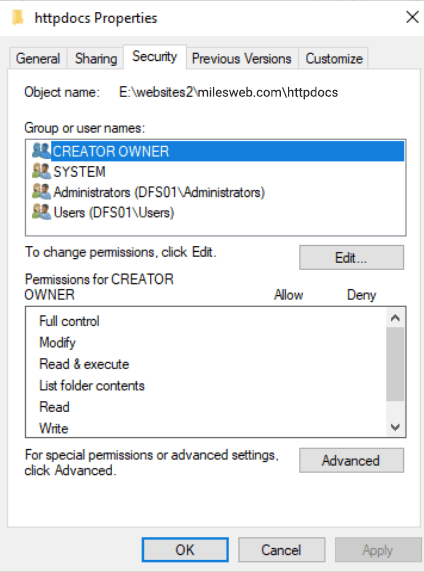
As mentioned, the “ApplicationPoolIdentity” user has very few permissions and so, the last steps is to make sure that the website files have been secured with the proper security settings. Go through your file system and search the folder where you plan on hosting your site’s files. Then right-click on the folder and select Properties. Here, go to the Security tab.
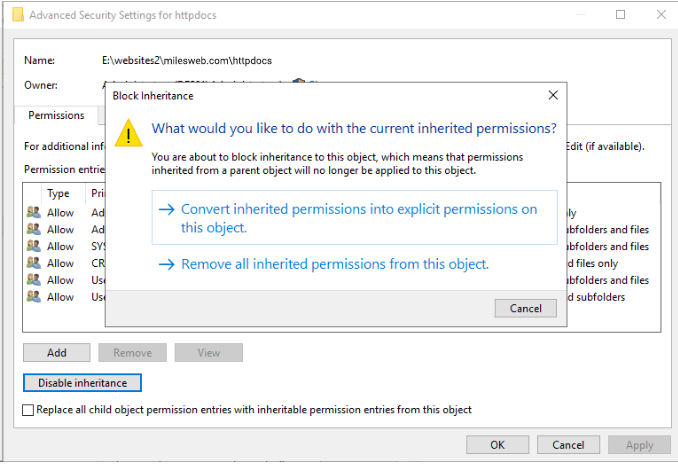
You will find several security permissions set up on the folder by default that aren’t essential and are potentially insecure. For securing your website, it is recommended to remove all but the “SYSTEM” and “Administrators” groups and add the “ApplicationPoolIdentity” user (and possibly any other user you want, such as an FTP user). But for doing this, you will need to disable inheritance. For this, click on “Advanced”, then click on “Disable inheritance”.
After this you will prompted for copying the current settings or starting with no settings. You can select any option, but, it is best to copy the current settings and then remove the unnecessary permissions. Therefore, select “ConvertConcert inherited permissions into explicit permission on this object” and then click on OK.
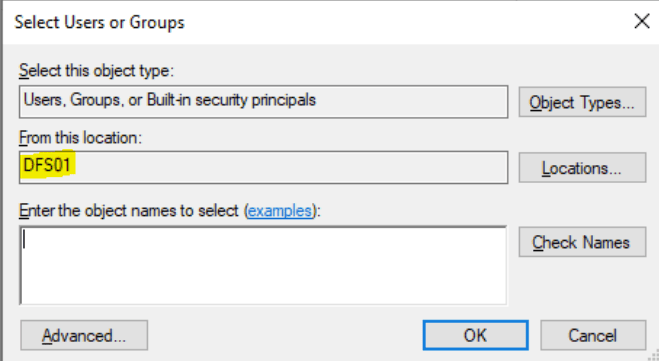
Now, you need to remove the unnecessary permissions. Click on Edit and remove everything other than the “SYSTEM” and “Administrators” groups. Then you need to add the “ApplicationPoolIdentity” user to this folder. For this, click “Add…”. Based on your server configuration, you might be prompted for authenticating to an active directory domain. Click the cancel button a few times until you get the Select Users of Groups screen as below.
Here, make sure that the “Location” selected is your computer. In case it’s not, click “Locations…” and select your computer (at the top; you might need to click cancel on some authentication windows here as well).
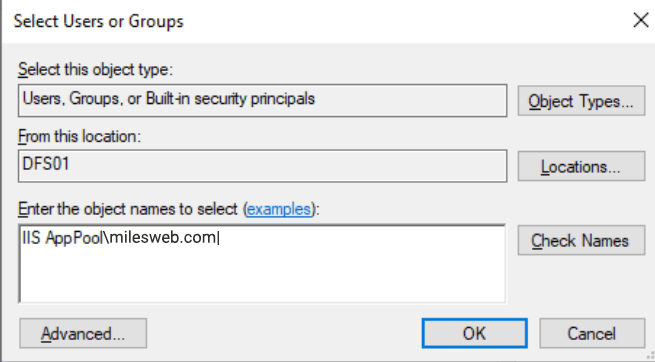
The “ApplicationPoolIdentity” user is a hidden user, so you can’t search for this user. For this, you will need to type the username to add it. You will need to type the username as “IIS AppPool\<applicationpoolname>”. Please check the following example and fill your information accordingly:
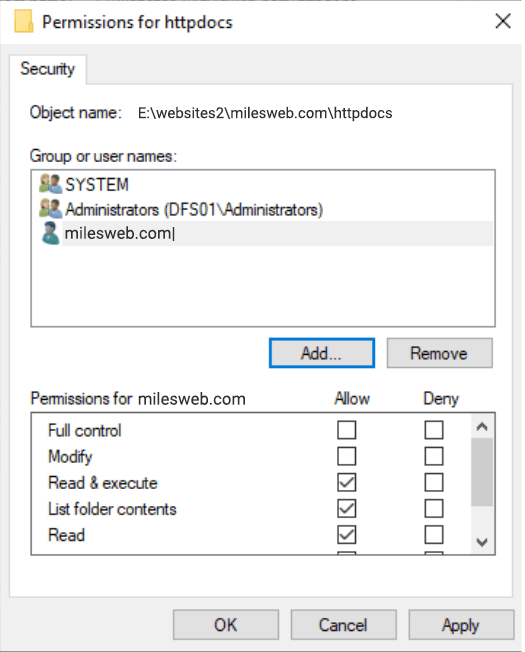
After you type the user name, click on OK. After adding the user, that is by default only granted read permissions, check your security settings if they appear similar to the following image, and then click on OK.
Now, you have a secure site ready to be viewed by others without worrying about the hackers.
Securing within Powershell
In case you’re looking get known to some Powershell, the steps covered in this article are also applicable for Windows Server 2012 or newer server through Powershell. Just fill out the first two variables with your domain name and the path to your content, and then run the remaining PowerShell commands to set up the site in IIS and configure folder permissions.
[String]$Domain = ‘’
[String]$Root = ‘’
Import-Module WebAdministration
#Create App pool & Website New-WebAppPool -Name $Domain New-Website -Name $Domain -HostHeader $Domain -PhysicalPath $Root -ApplicationPool $Domain Set-WebConfigurationProperty -Filter system.webServer/security/authentication/anonymousAuthentication -Location $Domain -PSPath MACHINE/WEBROOT/APPHOST -Name userName -Value ''
#Optionally add www. Binding New-WebBinding -Name $Domain -HostHeader www.$Domain -ErrorAction
#Remove inheritance (copy)
$ACL = Get-ACL $Root
$ACL.SetAccessRuleProtection($True,$True) | Out-Null
$ACL.Access | ?{ !(($_.IdentityReference -eq 'NT AUTHORITY\SYSTEM') -or ($_.IdentityReference -eq 'BUILTIN\Administrators')) } | %{ $ACL.RemoveAccessRule( $_ ) } | Out-Null
$ACL | Set-ACL
#Add IIS user permissions
$ACL = Get-ACL $Root
$acl.SetAccessRuleProtection($False, $True)
$Rule = New-Object System.Security.AccessControl.FileSystemAccessRule("IIS AppPool\$Domain", "ReadAndExecute", "ContainerInherit, ObjectInherit", "None", "Allow")
$acl.AddAccessRule($Rule)
$acl | Set-Acl
Additional Notes: In some cases, sites might require additional write or modify permissions on specific files or folders for cache files, file uploads, or other content. You should not apply modified permissions to the complete site. Instead, alter specific directories or files as needed. For applying these settings, go to the file or folder that needs modification, right-click on it, and select Properties. Jump to the Security tab and click on Edit. Then select the user comprises of the name of the website (milesweb.com in my example above), under the Allow column select modify, and then click OK. This will give the ApplicationPoolIdentity and IIS will be able to write to or modify the file(s) or folder(s).
In this way you can secure your website in IIS.